What is Removal Bits?
Removal Bits is not just another anti-malware website. It is the place where you can find various solutions to your problems related with malware, Trojans, adware, spyware, browser hijackers and toolbars. Our step by step removal guides are professionally written by highly qualified IT experts. With the help of our instructions, even the novice user will be able to get rid of malware within a few minutes. Removal Bits will teach you how to secure your computer and it is easier than you think.
Fresh virus removal guides
Removal Bits will keep you updated with information about the latest malware, virus attacks, security issues and tips. All of that you can find in our Malware News section. If you are looking for simple and clear, step by step tutorial on how to remove adware, spyware or browser hijackers, please visit the Malware section on our website. In the Popular Malware Files you will find the list of the most famous viruses, Trojans and other malware and of course our professional removal instructions.
We care about our customers and that’s why we are open for any questions. If you couldn’t find the solution to your problem on our website, just contact us and we will provide you with removal guide written by our specialists. Your problem may help others to fix their problems as well.
All of our removal tutorials are tested by our team and all of the removal tools provided on our website are totally genuine and verified for integrity. Also, we are constantly updating them and checking for viruses to guarantee the best security for our customers.
Get rid of malicious programs easily
Get rid of adware, malware, spyware, trojans , worms, rootkits and toolbars. Removal Bits will help you to clean your pc with step by step removal instructions for the newest infections.


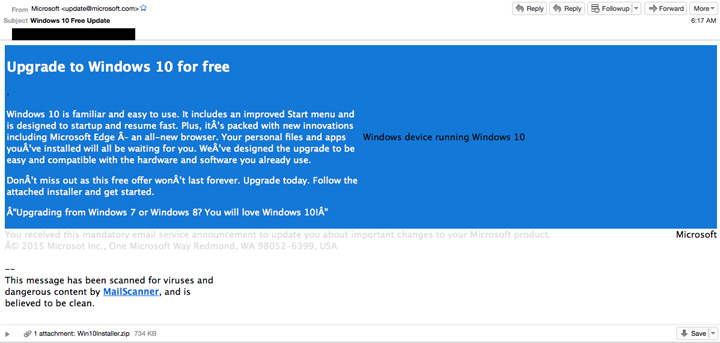
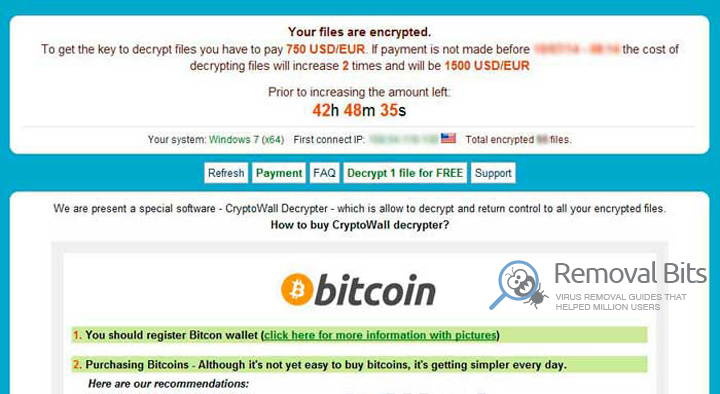

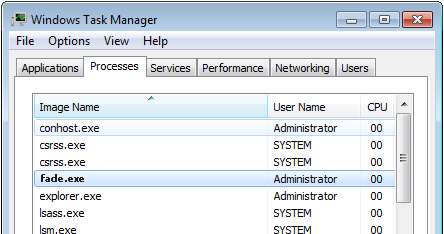

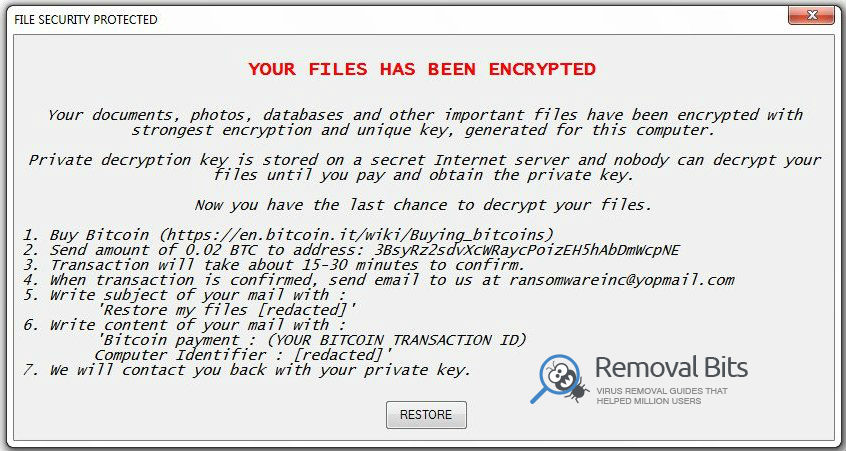






I am so thankful for this guide. I was seconds away from formatting my hard drive on my laptop when I found this guide. It was totally free and easy to follow. Thanks from one happy guy and his malware free computer! – Lukas Foerster
Thanks for taking the time to make this working guide. It was very helpful – Anne F. Gosselin
Thank you – this was very complete and most importantly – it worked. Other things I tried, including through my Internet service provider tech support did not work – Mike Black
This was fast, easy and found all of malware! Thanks a million! – Kiera Byrne